Take care of the security of your business
In 2020, hackers attacked over 64% of businesses. Although progressive digitisation and transferring the operations to the internet offer an opportunity for rapid growth, they also pose numerous threats. Ignorance and lack of awareness of such phenomena make a business an easy target for cybercriminals.
The danger awaits not only large international organisations, but also small and medium-sized businesses, which usually have poorer security and are easier to trick.
Why APT Defend?
We have created a unique solution that supports the process of building awareness of cyber threats among employees.
APT Defend means:
- a wide variety of possibilities of simulated hacking attacks carried out by cybersecurity specialists,
- safe training in the most common threats from criminals, enabling the adaptation of systems to the adequate response to an attack,
- access, at any time, to extensive knowledge on cyber threats in a convenient form of e-learning,
- a flexible tool enabling you to adjust simulation, training and security policy to the individual needs of your business. We show you exactly where the weak points are to increase emphasis on protection in these areas.
APT Defend is a product based on the expertise and experience of Polish security specialists. Each country has its own specifics to which criminals adapt. Thus, our Platform is adjusted to the threats present on the Polish market. The system monitors the situation in the network on an ongoing basis and adjusts its capabilities to changing trends.
Cyber (hacking) attack simulation
Since people learn the fastest through experience, simulating a hacker attack is one of the most effective methods to protect yourself against cybercriminals. By simulating hacker actions in a safe training environment, and then trying to control such an attack, you are able to make the organisation more aware of potential sources and methods of attacks, draw the right conclusions, and adjust your security systems and procedures. Such real-life training has much more effect than yet another e-learning as part of the employee training system
How can cybercriminals threaten your business? Find out about their methods:

Phishing
It involves various social engineering methods that enable hackers to access sensitive data. Most often, these are deceptive links in email correspondence or bogus websites

Smishing
A sophisticated form of phishing. It uses text (SMS) messages to trick the victim into providing confidential data. One of the recent very popular methods was a text message with information on an additional fee for your courier delivery

USB dropping
Some criminals use electronic equipment that they plant on the company's premises, which gives them access to valuable information once a certain file is opened on the device by employees who are totally unaware of the scam
"During the pandemic and remote work, the APT Defend platform helped us to determine the level of awareness of cyber threats among our employees in many countries in which we operate. These data allowed us to better tailor the educational materials and improve the effectiveness of the awareness campaign being implemented."

— Andrzej Piotr Kleśnicki, Global Information Security Director
Here comes our APT Defend solution
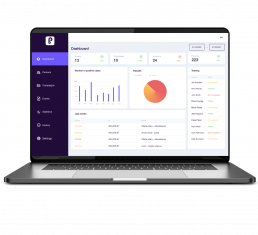
APT Defend console
It is used to manage simulated hacker attacks and is the central place of our system. This is where the creation of a simulated hacking attack begins. Of course, for educational purposes, such an attack is not real, although it is very much like a real one.
An important feature of the APT Defend console is the ease of creating simulations. The system contains a database of attack scenarios that determine the manner of conducting phishing campaigns. We can also create individual scenarios for you. After selecting the relevant scenario, you will be able to import the list of people to be trained in a very quick and intuitive manner. Creating your first campaign will take you less than 15 minutes!
Following the simulation, the console enables you to carry out an extensive analysis of the attack effectiveness and to draw users’ attention to which elements proved to be critical, and as such, require additional training. After conclusions have been drawn, you will be able to carry out further simulations based on a different scenario.
Two-Factor Authentication (2FA) scenarios
It might seem that two-step verification (e.g. login and confirmation of identity via SMS) ensures security and eliminates phishing threats. However, in reality, it is not that simple. APT Defend provides unique scenarios enabling you to have a full simulation of a hacker attack, even when using two-factor authentication. This is done using the integration with the Modlishka system, which, in simple terms, acts as a reverse proxy. Thus, it is an intermediate element between the client’s application and the server and could be used to intercept data even with two-factor authentication.

We have been using APT Defend in the process of building awareness of cyber threats for almost two years. Regular training and simulations of attacks carried out using the platform contributed to the minimisation of the number of phishing incidents.

— Krzysztof Szczepański, CSO
Discover new possibilities

Scenario templates, including customer-dedicated, with the possibility of self-configuration

Campaign support for PCs, laptops, phones and tablets

E-learning materials with interactive content

Ability to create your own educational materials

Configurable educational tests

Multiple language support

Addressing legal requirements such as GDPR and KNF (Financial Supervision Authority)

Dedicated phishing domains

Ability to brand customise scenarios (e.g. add a company logo)

Overall report summarising the results of the campaign

Export of reports to PDF or Excel

“Organisational resiliency” – an organisation's attack resilience report
Threat level metrics

Employee attack reporting function

Customer support service
Who are we?
APT Defend is a platform that combines high efficiency of operation and intuitiveness of use. It would not be possible without professionalism, passion, uncompromising attitude and focus on quality that characterise the APT Defend creators. Behind our solution stands a team of cybersecurity enthusiasts who have devoted most of their professional lives to improvement in this subject area. Our strength is the composition of our teams, made of people with different experience and ideas while striving for a common goal. This is the perfect recipe for creating universal and effective IT systems.
Andrzej Nowodworski
His professional interests are centred mainly around offensive security and securing cloud solutions. In the past, head of the IT Security Department of one of the largest Polish banks. He is well aware of the threats related to the development of new technologies and uses this expertise to help various institutions to defend themselves against them.
Each member of our team is a cybersecurity expert and has contributed his/her unique skills that enabled us to translate the system into a business solution. As a result, we are able to comprehensively help you and your business to learn the secrets of cybercriminal defence. IT security is a complex issue, the understanding of which requires many years of practice. Our system allows you to redirect the knowledge and skills of experts to locations that should be carefully secured.
Try APT Defend for free
Subscribe to our newsletters
Contact
office@aptdefend.com
+48 22 122 85 97
Office
Puławska 12/3
02-566 Warsaw
Poland




